Sender domains have been available for SMTPeter for a while now. With sender domains, it is no longer needed for users to set up their own SPF, DKIM and DMARC records, and it makes sure everything gets sent with the same domain name. Now, we've made it possible to see DMARC reports in the sender domains interface as well. Because they are parsed, they are way easier to read and more meaningful.
What are DMARC reports?
When you've got DMARC set up, you will receive daily (or more frequent) DMARC reports from companies like Google, Yahoo! and Microsoft. These reports hold, among other things, information about the amount of IP addresses that received the mailing and whether they passed the DKIM and SPF authentication tests.
Thus, DMARC reports can show how your mailings are doing, authentication-wise. If invalid IP addresses are sending email using your domain, this could mean one of two things: either someone who is allowed to send these mails does not have their stuff together, such as a coworker who hasn't updated their email system, or somebody who is not allowed to send these mails is doing so anyway, pretending to be you. In both cases, insight in the situation can help fix the issue.
The problem with unparsed DMARC reports, however, is that they can be hard to decipher if you're not particularly skilled at reading code. That's why SMTPeter now deciphers them for you by showing the parsed report, along with a description of the current policy.
The interface
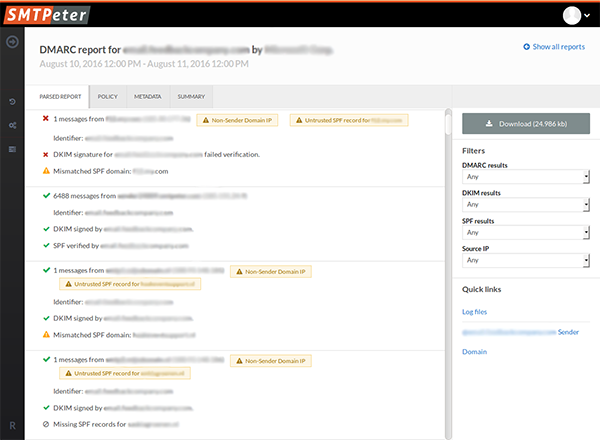
This parsed report shows the IP address every message was sent from. It shows what went right, what requires attention and what went outright wrong, so you know what to focus on when altering your settings.
The 'policy' tab shows the policy the recipient read in the DNS of the sender when it got their emails. It holds the domain, DKIM alignment policy, SPF policy and more. This way, you can directly see the connection between the results you got and the policy that was set at the time, and adjust appropriately. The 'Metadata' tab provides information on the sender of the DMARC report, its ID and the date range of the report.
We've also interpreted the data into something a lot more clear than just a list of all individual mailings: a summary of the report. In the summary the total amount of processed messages and the percentages of messages that succeeded and failed are shown.
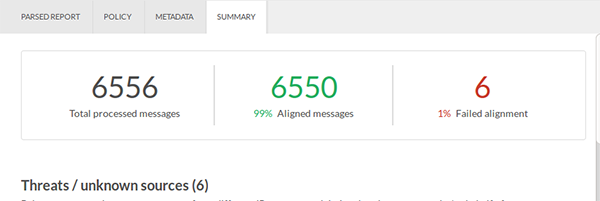
Beneath that is a list of threats/unknown sources. It shows the IP, the amount of messages and the issues that source has. Based on this, you can judge for yourself whether these sources are actually threats or just somebody without proper configuration. Below that is a list of trusted sources.
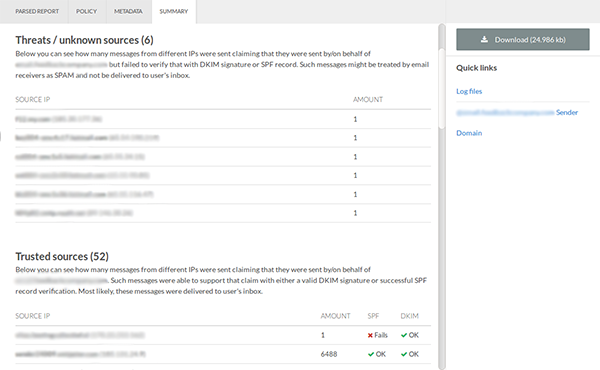
If you do want to see the original, unparsed report, it's possible to download it to your computer.
